
With the ease of availability of information about email scams the numbers of businesses who's emails are being compromised continues to steadily rise. Email-borne it security risks include viruses, scams, phishing attacks and more. Knowing how to protect yourself against these attacks is challenging because hackers are dynamic and smart about how and who they target, making it difficult to know what is and isn’t legitimate
In this post we help you to help yourself by pointing out a few common email threats and how you can identify them.
That looks a bit dodgy – how to spot suspicious emails
Emails are still one of the biggest vectors for malware and, as much as you’ve probably read this a billion times before, every day networks get compromised because… people open emails that they shouldn’t!
So, what should you look for?
- Emails that come from known senders with attachments and links that don’t conform to an expected norm, such as format, greetings, content (one example would be getting emails from yourself!)
- Emails from unknown senders
- Emails that address you in an unusual way (e.g. Dear Davidq)
- Emails that have no greetings or introduction at all
- Emails that suggest that you have an issue that the sender will fix
- Emails that ask you to sign up to a website
- When they seem too good to be true such as “you won a prize” type of emails… that’s probably because they are!
- Emails from unknown senders that have an ‘invoice’ or ‘credit note’ attached.
If you notice any of these unusual things, the message is pretty simple: do not open, do not respond, do not forward.
Don’t click – and don’t be curious
If any of these things pop up on your inbox, the message is simple: delete them immediately. Whatever you do, DON’T click on any links, open attachments or follow instructions to win a prize unless you are sure that the email is legitimate. If in doubt…DELETE.
Curiosity killed the cat, they say, but it can also kill your computer and the network. Hackers cleverly try to pique your interest – don’t fall for it. That ‘invoice’ or ‘tax refund’ that you open can make your life very difficult,
Some examples to help you help yourself
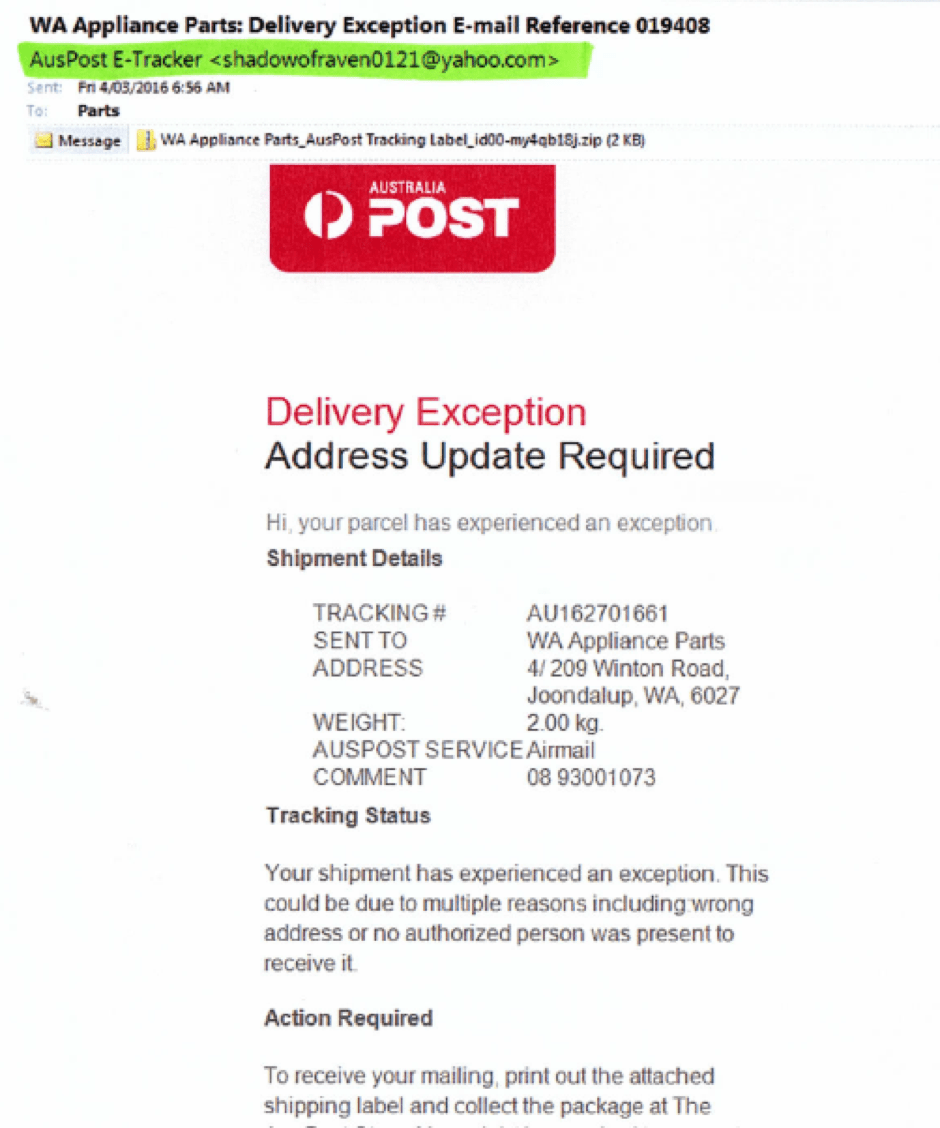
There are plenty of examples of the threats; a recent case involves Australia Post asking the email recipient to update their address to receive a parcel. As you can see the email looks legitimate, however when you look at where it has been sent from this should trigger alarm bells!
Earlier, in February, an email purportedly from ‘Microsoft’ congratulated recipients for winning an internal promotion. Hint: it wasn’t Microsoft sending the email and the promotion never existed.
These and plenty more examples can be found on the Australian Governments’ Scamwatch website and if you think that you’re subject of a scam, you can report it through their simple report function.
Err on the side of caution
The final note is a simple one: rather err on the side of caution than open something which looks tempting only to find it is a virus, phishing attack or other malware. DELETE should be the default action for any emails which look even slightly dodgy. That’s a far safer course of action than opening it up and opening yourself to compromise.
