
Australia Post has an interesting way of assessing their internal IT Security – internal phishing campaigns. These campaigns are designed to test staff and their awareness of Security issues; as well as the steps that they would take when they think they spot a nefarious email.
When Australia Post’s campaign was launched last year they were met with staff who said that they weren’t stressed about the potential of this breach (at least half of the staff included.) This has hugeimplications for any organisation, especially one the size of Australia’s Post Network.
The way in which the phishing campaign had been engineered was that if a user clicked on the foreign link they would be redirected to Australia Post training (unfortunately this was abandoned within 30 seconds of clicking). Adam Janik, who heads up the Information Security team at Australia Post, both realized that they needed to shake things up a bit to get the right attention.
The team realized that this wasn’t the most effective way to educate their staff as they were becoming increasingly disengaged as time went by. They identified that redoing the training material wouldn’t be effective, more education around identification might work (but most employees stated that they could spot the emails). So what were they to do?
Ransomware.
This type of attack (click here to read more about Ransomware) is less familiar to Australia Post recipients but according to Janik and other leading Security Experts, is growing in scale and severity.
The team at Australia Post created their own fake ransomware to command the full attention of staff and educate on the real and damaging risks associated with this type of malware.
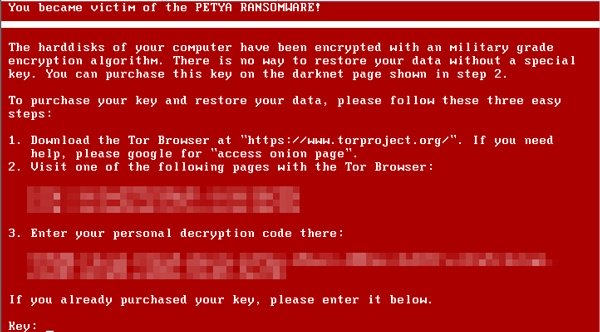
The warning screen of the attack used black and red colouring with the image of a skull and crossbones to really give the simulation credibility. The ‘ransomware’ ran for 18 seconds before taking users to training material. The 18 seconds was just enough time for people to realise that this was a serious threat and that there will be real ramifications for what they have done.
What they found from a small trial group of the ransomware was very interesting. From a control group of 12 users accompanied with a Security team member present to field questions if they arose, participants stress levels rose to high levels when assessing them out of 5.
For this reason the Information Security team at Australia Post decided not to make this an organizational wide initiative, yet. They will approach Ransomware as they did Phishing and slowly implement this type of simulations when staff are more educated about the ins and outs of this cyber threat.
All businesses need to be aware of the very real threat that Ransomware can have on organisations of all sizes. In March last year, there was a reported 56,000 infections in the U.S alone. These numbers are set to rise with hackers steadily becoming more and more sophisticated and businesses responding with little to no action.

