We’ve all heard about phishing emails, but what about vishing? 📞 That’s short for voice phishing. It’s when a cyber criminal calls you and pretends to be someone else, like an IT technician, a bank employee, or even a government official.

Don’t let a phone call catch you out

What’s on your Windows Clipboard?
📋 Have you ever thought about what’s sitting on your Windows Clipboard? Most of us never even consider it, right? It’s that handy little feature that remembers the last few things you copied. Like text, links, images, even screenshots.

Need more AI training? You’re not alone
AI is no longer something we need to consider in the distant future. It’s already here, reshaping how we work today. But new research shows that getting started with it is more challenging than many expected The study gives us some interesting insights: 28% of small and medium-sized businesses say that not automating is hurting […]
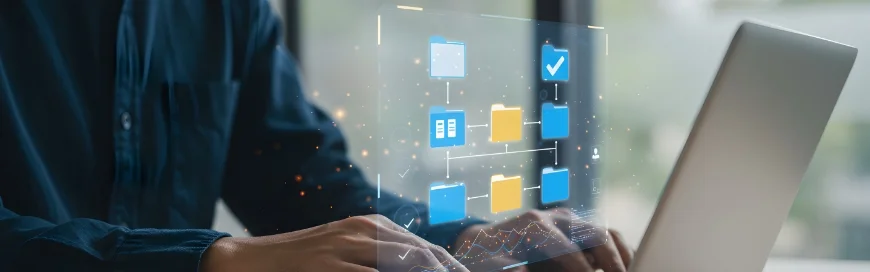
Do your staff have too much access to data?
This should make you stop and think for a moment. Do you know everyone that has access to your critical data right now? And do they need that access to do their job? Most business owners assume that access is finalised during the onboarding process.

Could your business get more from AI?
AI has certainly arrived and feels like it’s everywhere right now. With smart tools showing up in our inboxes and new features in our favourite apps. But you may be surprised to know, most small businesses are not ready to maximise its benefits.

Email is still #1
When it comes to business communication, we’re a bit spoilt for choice these days. With AI tools, instant messaging apps, and collaboration platforms, you’d think email would be on the way out, right? Not anytime soon 📧 The State of Business Email report is based on insights from over 4000 IT leaders around the world.

Is your new hire a security risk?
When you bring someone new onboard, do you think how it may affect your security posture? Most business owners focus on helping the new starter settle in and making sure they have what they need. Things like a laptop, email account, access to the appropriate systems, and a quick intro to the team.

Is your microphone listening?
When sitting in your office, you would consider your conversations to be private. Whether you’re on a video call or speaking with someone in person. Most of us would be confident that the walls would stop any potential eavesdroppers. Well…that may not be the case 😳 Researchers have found a way that cyber criminals could […]

Notepad gets some new formatting tools
Ever wished you could slightly format your notes in Notepad, with bold text or a heading? Well, you’re in luck. Microsoft is giving Notepad a little upgrade. This could make quite a difference for those of us who still use it to jot down notes, meeting minutes, or quick checklists.

A new naming system for hackers planned by Microsoft
Imagine trying to follow a movie where the villain goes by four different names. It would be a bit confusing to say the least. That’s what it’s like in the cyber security world right now. A hacking group could be referred to by completely different names, by those who report and write about them.

